13,614 views
 Nessus/OpenVAS wrapper for ike-scan
Nessus/OpenVAS wrapper for ike-scan
ike-scan is a great tool to audit VPN/IPSec implementations. This tool, which runs under Lunix, Unix, MacOS and Windows, can be found at www.nta-monitor.com/tools/ike-scan/ (Latest version at time of writing is 1.9). My Nessus ike-scan NASL wrapper may or may not work with earlier versions or newer versions, so test test test)
Some of the great features of ike-scan include extracting the PSK, or transform attributes to find all algorithms that are enabled on a device. Especially this last function may require some scripting and lots of time to go through the log files in order to see whether your solution is configured the way it should be configured.
So I decided to write a nessus nasl plugin to run ike-scans.
The plugin is in fact a wrapper around ike-scan and will parse the output, looking for specific settings :
- Does the VPN implementation allow aggressive mode ? (this will generate a security_warning)
- Can the PSK be extracted ? (and maybe brute-forced with psk-crack or other tools) (this will generate a security_hole, however if you must use a PSK as sole authentication mechanism, make sure it is very very very long)
- Is DES, MD5 or DH Group1 being used (which are considered to be a lot less safer and secure than for instance 3DES, SHA and DH Group2) (this will generate a security_hole, because it is not safe to use these algorithms/selections at all)
- KeySize : if a keysize (f.i. keysize of AES) can be captured and is found below a given number of bits, a security_hole notification is generated. (Default audit will look for a keylength of less than 128 bits, but this is configurable)
- Display all proposals that were used in successfull handshake attempts
In addition to this, the wrapper will attempt to find and display the device vendor. (will generate a security_warning)
All of these tests are hardcoded in the script, so if you want to look for different things, feel free to edit the plugin.
Both Nessus (www.nessus.org) and openVAS (www.openvas.com) are Network Vulnerability Scanner, free to download, offering various sets of plugins for Home Users and Professionals. My nasl plugin does not depend on existing or new plugins, so you can run the plugin with both free and paying plugin subscriptions.
Before you begin
I will explain some configuration specifications for Nessus, I’m sure you can figure out yourself how to achieve the same goal in openVAS.
This plugin requires some specific settings to be configured in nessus. First of all, since the plugin is not signed, you will need to edit nessusd.conf (/opt/nessus/etc/nessus/) and all non-signed scripts :
nasl_no_signature_check = yes
If you want to use the transform functionalities and vendor fingerprinting (via the backoff technique), you will need to configure nessus to allow a long plugin timeout. Both of these functionalities can take a long time to complete, so I would advise you to change the plugins_timeout value in nessusd.conf and set it to a high value (f.i. 1800 seconds)
plugins_timeout = 1800
(Note : starting from version 1.0.8, you don’t need to do this anymore. The plugin timeout is now set to unlimited, so you don’t need to worry about the scan not being able to complete in time)
Finally, (and of course) “ike-scan” must be installed on the system and must be in the “path”. Nessus runs as root, so you must verify that you can run ike-scan as root.
Installing the plugin
Download the .nasl script (zip file) from the link at the bottom of this page, unzip it and place it in the nessus plugin folder (/opt/nessus/lib/nessus/plugins)
The plugin file is called ike-scan-wrapper.nasl
Stop the nessus service
/etc/init.d/nessusd stop
Start the service again, and load the new plugin at the same time
/opt/nessus/sbin/nessusd –t –D
Using the plugin
In this post, I will use the Nessus client for Windows to illustrate the usage, but everything should work exactly the same way when running the client from a different OS
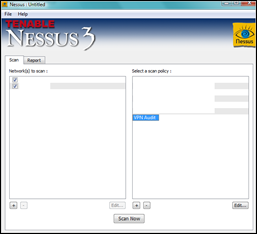
Create a scan policy by clicking on the + sign at the right hand side
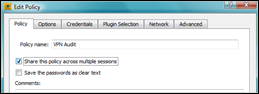
Set a name and enable “share this policy across multiple sessions” if you want to keep the settings for future scans
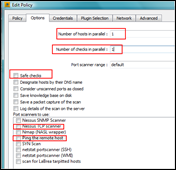
Under “options”, make sure to set the number of hosts and checks in parallel to 1. This is mandatory, because it is not possible to run multiple ike-scan instances at the same time if they use the same local port (udp/500) (You can, however, set the source port to 0, which will force ike-scan to take a random high port, so you can run multiple tests simultaneously. On the other hand, the remote device may require that you use source port 500 as well, so you’ll have to take this into account)
The plugin does not rely on portscanner results, so disable the portscanners and host ping. So even hosts that do not respond to a UDP port scan to port 500 can be audited with this plugin
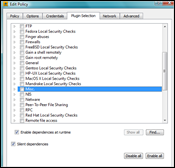
Go to the plugin selection page and click “disable all”. Verify that all sections are disabled.
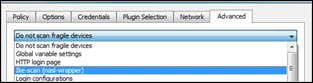
Navigate to section “Service detection”, open the section and select the ike-scan (nasl-wrapper) plugin.
Go to the “Advanced” tabsheet.
Select the Ike-scan (nasl-wrapper) entry from the dropdown list
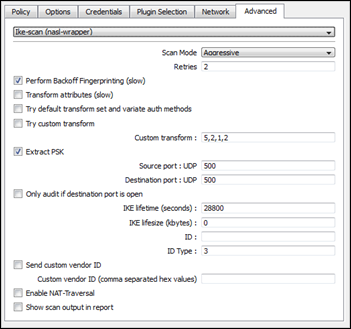
These are the default options :
- Scan mode : aggressive (you can select main mode as well, but testing for aggressive mode may be your first test, as this mode is less safe than main mode)
- Retries : 2 (if you increase this value, results will be more accurate (if you are auditing hosts via an unreliable link), but it will slow down the scan against non-responsive hosts.
- Backoff fingerprinting enabled (this will slow down the scan, but you will get a device vendor guess. If you are not interested in the vendor guess, disable this setting)
- Transform attributes disabled (this will also slow down the scan, but it will give you the most accurate results). The default setting is set to disabled, but it may be a good idea to enable it.
- Encryption algorithms, Hashing Algorithms, Authentication Methods and Diffie-Hellman groups : please visit the ike-scan website to understand what these strings are and how to use them. Just make sure to separate entries with a comma and not to use any spaces. You can use these fields to limit the algo’s/methods while transforming attributes.
- Try default transform set and variate auth methods : this options is disabled by default, because it will slow down the scan. Using this option can be enough to already identify a VPN vendor (and/or find some obvious proposals).
- Try custom transform : you can specify a set of encryption/auth/hash/dh group parameters to further audit one particular proposal. Have a look at the ike-scan wiki to find more information about these values and what they mean.
- Extract PSK is enabled by default. (PSK extracting will only work in aggressive mode. So even if the option is enabled for main mode, no output will be returned)
- Source and destination port are set to UDP 500 (for maximum compatibility). As stated earlier, if you set the source port to 0, ike-scan will take a random high port number, allowing to run multiple scans at the same time, but you have to verify that the remote device supports this.
- If you have a UDP scanner in Nessus, you can enable “only audit if destination port is open”, but generally this is not needed.
- IKE lifetime set to 28800
- IKE lifesize set to 0Kb (= disabled)
- ID and ID Type : see the ike-scan wiki for more information on these fields (ID = Group ID. You can specify multiple group IDs by separating them with a comma. Note : ID only works in aggressive mode)
- Send custom vendor ID : if you want to send specific vendor ID or ID’s, you can enable this option and enter the hexadecimal vendor ID in the custom Vendor ID field. If you want to try multiple vendor ID’s, then enter the various IDs and separate them with a comma. Make sure not to use any spaces in this field.
- Enable NAT-Traversal (disabled by default)
- Show scan output in report : disabled by default. Especially if you scan with most options enabled, this report may become quite lengthy, but on the other hand, you’ll have the output of all handshakes that were encountered during the scan, together with the transform that was used.
(note : this screenshot may be somewhat outdated – depending on the version that you are using)
Click Save
On the main page, on the left hand side, add the hosts/networks you want to audit
Then, select the new policy on the right hand side again and click “Scan now”
Now wait
You can follow up on the scan process by looking at the following files (tail –f ) :
/opt/nessus/var/nessus/logs/nessusd.dump
/opt/nessus/var/nessus/logs/nessusd.messages
/var/log/messages
As soon as the scan kicks in, you should get something like this (in nessusd.dump) :
Initiating IKE audit
————————————–
ike-scan-wrapper.nasl[12037.14]>[+] Source port set to UDP 500
ike-scan-wrapper.nasl[12037.14]>[+] Destination port set to UDP 500
ike-scan-wrapper.nasl[12037.14]>[+] Target ip : 1.1.1.1
ike-scan-wrapper.nasl[12037.14]>[+] Nr of retries set to 1
ike-scan-wrapper.nasl[12037.14]>[+] PSK Dump/Extract enabled
ike-scan-wrapper.nasl[12037.14]>[+] IKE Aggressive mode scan enabled
ike-scan-wrapper.nasl[12037.14]>[+] Transform attributes enabled (scan will be slow, please wait)
ike-scan-wrapper.nasl[12037.14]>[+] Running ike-scan against 1.1.1.1:500
ike-scan-wrapper.nasl[12037.14]> -> Aggressive mode
You can follow the scan process (including all ike-scan parameters) in /var/log/messages
Feb 1 11:40:55 router-3 ike-scan[25601]: Starting: –retry=1 –sport=500 –dport=500 –lifetime=28800 –pskcrack -A –showbackoff –multiline –trans=7/192,5,4,7 1.1.1.1
Feb 1 11:40:55 router-3 ike-scan[25601]: Ending: 1 hosts scanned in 0.041 seconds (24.68 hosts/sec). 0 returned handshake; 1 returned notify
Feb 1 11:40:55 router-3 ike-scan[25602]: Starting: –retry=1 –sport=500 –dport=500 –lifetime=28800 –pskcrack -A –showbackoff –multiline –trans=7/192,5,4,8 1.1.1.1
Feb 1 11:40:55 router-3 ike-scan[25602]: Ending: 1 hosts scanned in 0.038 seconds (26.21 hosts/sec). 0 returned handshake; 1 returned notify
Feb 1 11:40:55 router-3 ike-scan[25603]: Starting: –retry=1 –sport=500 –dport=500 –lifetime=28800 –pskcrack -A –showbackoff –multiline –trans=7/192,5,4,12 1.1.1.1
Feb 1 11:40:55 router-3 ike-scan[25603]: Ending: 1 hosts scanned in 0.040 seconds (25.16 hosts/sec). 0 returned handshake; 1 returned notify
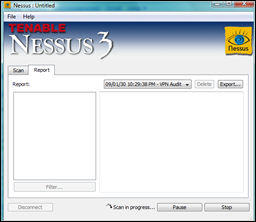
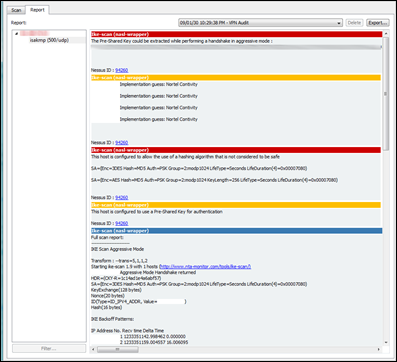
When the scan has completed, you should see the report :
(don’t pay attention to the Nessus-ID. I just used a random high number that is not linked or affiliated with Nessus in any way)
You may notice that the plugin for vendor guessing may output the same string several times. This is caused by the fact that, for every proposal that was found, backoff fingerprinting was executed. Sometimes, you will only find the vendor after one of the backoff attempts, so I decided to show all strings in the output, so you can decide for yourself.
Download
You need to be logged in to download this script. You can log in and/or register using the “Log In” link on the right hand side of this blog.
PVE ike-scan wrapper for Nessus/Openvas (6.9 KiB)Version updates
Current version : 1.0.9
Check back regularly to see if new updates are available.
Update history
1.0.9 : 18 march 2009 : fixed reference to ike-scan wrapper from openvas, and family statement
1.0.8 : Added reference to cve and set plugin timeout to unlimited
1.0.7 : Fixed typo in Nessus/OpenVAS family. Plugin now resides under “Service detection”
1.0.6 : cleaned up some code, fixed copyright statement
1.0.5 : feb 4th, 2009 : Fixed some minor bugs, added options (such as allowing the auditor to specify the list of encryption/hashing algo’s, auth methods and dh groups that can be used when transforming attributes; and speeding up the backoff vendor guessing process). The plugin ID was changed to 60001. Many thanks to Tim Brown for working with me on getting this version released.
1.0.4 : feb 1st, 2009 : Fixed a bug with hosts that do not respond anything at all
1.0.3 : Added some options, moved the plugin from “Misc” section to “PVE Custom” section
1.0.2 : First version released to public
Final notes
If you find bugs, let me know. (support forum)
If you like this plugin, let me know, and even more important : tell it to others !
© 2009 – 2021, Peter Van Eeckhoutte (corelanc0d3r). All rights reserved.