3,295 views
 HITB2012AMS Day 1 – Window Shopping
HITB2012AMS Day 1 – Window Shopping
Window Shopping: Browser Bugs Hunting in 2012
In the last talk of Day 1, Roberto Suggi Liverani and Scott Bell (not present during the presentation), security consultants at Security-Assessment.com, will share the results of some intensive browser bug hunting research, and will drop 5 0days.

Roberto starts by apologizing about the fact that Scott was not able to join him at the conference.
The agenda of the talk contains 3 major components:
- Introduction
- Window Shopping
- Conclusions
Introduction
Everybody uses browsers, Roberto states. Browsers have become predominant desktop applications and we see a clear shift towards client-side applications and attacks. It makes a lot of sense to take a look at the security of browsers.
Window Shopping
Firefox Use After Free < 11 (Fixed in FF11), found by Scott Bell.
This bug only works in Windows 7. Roberto mentions that it took the devs a long time to get fixed, indicating possible complexity involved with this bug. A slightly modified version of cross_Fuzz was used to find this bug.
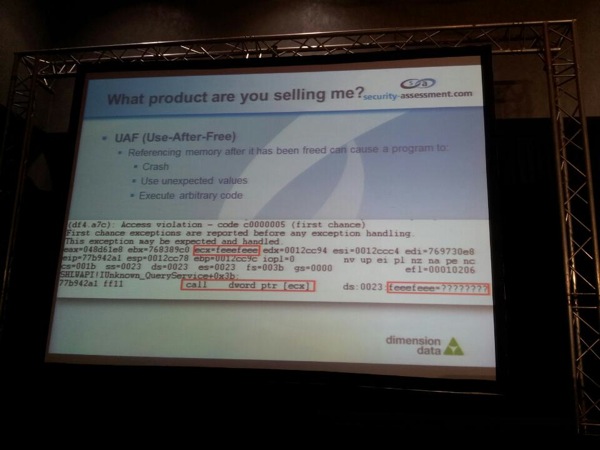
To make cross_fuzz produce the crash, they basically added more entropy, randomizing call parameter count, removed google_gc() and changed some other things. To create a different HTML file every time, they implemented HTMLGen. They also removed some phases in cross_fuzz to make things faster.
After triggering the crash, they had to simplify the html page that caused the crash and remove unnecessary components. Using the JSLOG Firefox extension, they logged DOM operations, allowing them to observe browser behavior around the time of the crash. FInally, they had to trace the browser behavior in a debugger… which took a fair bit of time (months). In the end, they were able to pinpoint the exact code that causes the UAF condition.
In terms of exploitability, they discovered that there’s some kind of race condition involved, making timings particularly important to gain code execution. The proof of concept code demonstrated on stage doesn’t include DEP/ASLR bypass either (it just sprays and ends up jumping into the spray).
Maxthon – XCS and SOP Bypass, found by Roberto
Roberto found a couple of bugs in Maxthon and first explains what a Cross Zone Scripting is and the fact that it offers and intrinsic Same Origin Policy bypass. If you have javascript running in a trusted zone (and each browser has a trusted zone), you can access the local system API’s. If you can do that, you can execute code, and it would be 100% reliable.
Maxthon, a chinese web browser, supports Trident and Webkit layout engines, and is used, according to Maxthon, by 130 million users. Roberto found 5 ways to get code execution in the Maxthon browser. In addition to the Trusted Zone issues (and the fact that they could inject code into the about:history page), they also discovered that i.maxthon.com appears to be a trusted domain, allowing access to privileged API’s. There’s no control on domain name to IP resolution, and no SSL either. MiTM anyone ? The latest version of the browser is still vulnerable to some of the bugs they found. To demonstrate code execution, he used a few lines of javascript that creates a .bat file, adds some commands into the file and then runs it.
Avant Browser XCS & SOP Bypass, found by Roberto
Yet another Chinese browser fell apart during their research. Roberto drops 3 0day bugs during the talk (because the Avant devs didn’t respond to any of his reports). Avant is a custom web browser application, using IE (light version) or IE/FF/Chrome (Ultimate) in the background. With 26 million downloads, the app seems to be used by a lot of people. Some of the files in the res folder are rendered in special pages, allowing for the execution of a privileged function (ARFunCommand()). They fuzzed the methods from this undocumented function and found some interesting results, returning information from the browser and browsing sessions. Using the 60003 value found during the fuzzing, they managed to perform a SOP bypass and XCS.
Firefox, patched in 3.6.14 – CVE 2010-1585
Roberto discovered that the nslScriptableUnescapeHTML.parseFragment() function, which is used to filter and sanitize data. Instead of using
Corelan Team Merchandise
Corelan on Slack
You can chat with us and our friends on our Slack workspace: