3,743 views
 How to properly restore (objects in) the 2003 AD database
How to properly restore (objects in) the 2003 AD database
Windows 2000 /Active Directory has been around for more than 7 years now. I’ve been using AD for almost 7 years, and due to its stability, I never had to recover a deleted object in AD. (Knock on wood). So it’s not a real surprise to find out that a lot of admins don’t even know how to properly restore a deleted object, or even restore AD the proper way.
First of all, you need to have a System State backup from your Domain Controller, created with ntbackup. This System state backup contains various components from that server (such as the registry) and also contains a snapshot of the AD database (ntds.dit). Before explaining how to use the System State backup to restore an object, it’s important to know that you will need to take down a DC in order to restore an object; and that you need to use the System State backup that was made on that DC. (Well, at least, that is the recommended way. There are ways to just recover objects using the ntds.dit file, but that procedure should be used in emergency situations only “when everything else fails”). Next, you need to know the Directory Services Restore Mode password. This password was defined when you ran the dcpromo. If you don’t know that password anymore, then you should change it prior to running the backup. This is how you can change the password :
| Open a command prompt and run “ntdsutil”
at the ntdsutil prompt, run “set dsrm password” If you want to reset the password on the current server, run “reset password on server null“. If you want to change the password on a remote server, run “reset password on server At the dsrm prompt, type ‘q’ and press enter. At the ntdsutil prompt, type ‘q’ and press enter. |
Due to the fact that you need to bring down a DC, it’s important to plan for this. If it is difficult to bring down a DC because you only have one DC, or if it is a problem to take down a DC because it is the PDC emulator, then you need to prevent this from becoming a problem by setting up a second DC. This will not only provide redundancy and load balancing for certain applications, but it will also allow you to take down that second DC without users noticing.
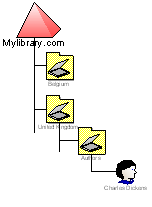
Case : suppose you’ve deleted a user account called “Charles Dickens” from the “Authors” OU, which is a child OU from “United Kingdom”. The domain in my example is called “mylibrary.com”, and the affected object tree looks like this :
The distinguished name of the object is CN=Charles Dickens,OU=Authors,OU=United Kingdom,DC=mylibrary,DC=com
In fact, when you want to restore a deleted user object, you have 2 options : either use ldp to de-tombstone the object, or use an authoritative restore of the object. If you choose to use ldp, check http://support.microsoft.com/kb/840001/ . This procedure requires you to have documented the group membership of that user. Also, the password will not be restored and as a result, the object will be disabled. That procedure does not require you to take down a DC, but as explained, you need to have documentation. Alternatively, if you did not document anything and you don’t want to take down a DC, you can use this procedure to use one of Longhorn’s (Windows 2008 server) features to get the information you need.
Anyways, I’ll use the authoritative restore method this time.
Last quick note before proceeding with the restore : When an object is deleted in AD, it’s not gone yet. It is tombstoned and will only vanish completely after a while. So the object is still there, and has a specific USN.
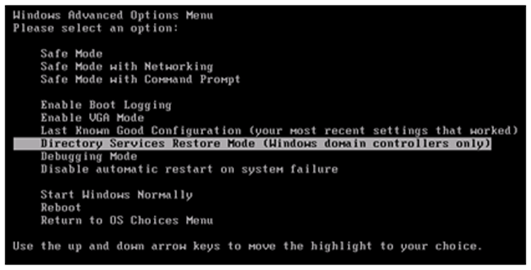
First of all, restart the DC (the one used to create the AD System State backup (.bkf) file). At boot time, press F8 go enter Directory Services Restore Mode
Wait until the system boots, and log on with “administrator” and the Directory Services Restore Mode password. Accept the warning about “Safe Mode”
Use ntbackup to restore the System State to the server. Choose to “restore to the original location”, and “overwrite existing files”. Also, ensure to “restore junction points”
When the ntbackup restore process has completed, do NOT reboot the machine. You have now essentially overwritten the existing ntds.dit file with an older copy of the file. At that point, the USN of the object is lower than the USN of the tombstoned object, so if you restart the DC, it will not only receive all updates from other DC’s, but the user object will be overwritten by the tombstoned object. Result : the object will be deleted again. So before rebooting and enabling replication again, you’ll need to update the USN of that object, so it becomes “authoritative”.
| Open a command prompt and run “ntdsutil”
At the ntdsutil prompt, type “authoritative restore” Type “restore object In our example, the command would look like this : restore object CN=Charles Dickens,OU=Authors,OU=United Kingdom,DC=mylibrary,DC=com This will increment the USN with 10000. If you’re not satisfied with this value, you can use the verinc parameter in the “restore” command to specify your own value. Example : restore object CN=Charles Dickens,OU=Authors,OU=United Kingdom,DC=mylibrary,DC=com verinc 11111 Type quit to exit authoritative restore mode and Type quit again to exit ntdsutil. Reboot the DC, let it start as a regular DC (not in Restore Mode) and check replication. If all goes well, your object will re-appear in AD and will still have all attributes set. |
If you want to delete an entire OU and everything below, you can use the “restore subtree” command (followed by the distinguished name of the OU). If you want to restore the entire AD, you can simply use the “restore database” command.
© 2007 – 2019, Peter Van Eeckhoutte (corelanc0d3r). All rights reserved.
Similar/Related posts:
 Restoring 2003 AD Objects using Windows 2008 Server
Restoring 2003 AD Objects using Windows 2008 Server
 How to restore a Windows 2003 DC using ASR and VMWare
How to restore a Windows 2003 DC using ASR and VMWare
 AD 2003 DC Restore Technique using VMWare (without having to grant local DC/Domain Admin rights)
AD 2003 DC Restore Technique using VMWare (without having to grant local DC/Domain Admin rights)
 Exchange 2007 : Powershell script to select optimal database for a new mailbox
Exchange 2007 : Powershell script to select optimal database for a new mailbox
 Backup & Restore Windows Server based Print Servers
Backup & Restore Windows Server based Print Servers
Comments are closed.
Corelan Training
Check out our schedules page here and sign up for one of our classes now!
Donate

Your donation will help funding server hosting.
Corelan Team Merchandise
Corelan on Slack
You can chat with us and our friends on our Slack workspace: