76,497 views
 Juniper : Setting up an IPSec VPN tunnel between a Juniper Netscreen firewall/vpn device and a Cisco VPN device
Juniper : Setting up an IPSec VPN tunnel between a Juniper Netscreen firewall/vpn device and a Cisco VPN device
Today, I will explain the (easy) steps to set up a route-based IPSec VPN tunnel between a Juniper Netscreen firewall/VPN device and a remote Cisco device (such as Cisco ASA)
If you are looking for more generic information on IPSec and building VPNs with Juniper, take a look at my blog post on VPNs with Juniper netscreen : Building IPSec VPN with Juniper Netscreen ScreenOS (CJFV)
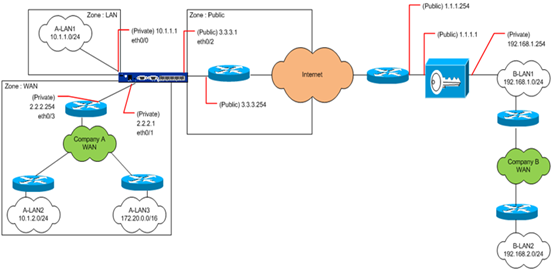
The example network used in this explanation looks like this :
These are our goals :
-
Set up a two-way VPN between company A (behind the netscreen device) and company B (behind a Cisco device), using PSK, 3DES/SHA1
PSK (Pre Shared Key) : AD230LdaiJDIdaz392382
- Set up bidirectional routing from A-LAN1 to B-LAN1 and B-LAN2, no network address translation
- Allow hosts from A-LAN2 and A-LAN3 to access B-LAN1 and B-LAN2, and use the netscreen firewall interface IP address in the WAN zone (eth0/1 : 2.2.2.1) as source IP address
The public (internet) IP addresses of each vpn device are 3.3.3.1 (Netscreen, Company A) and 1.1.1.1 (Cisco, Company B)
I’m not a Cisco expert, but I can confirm that the setup on the Cisco device is pretty straightforward. You need to define the local and remote network objects (ACL), define Phase 1 and Phase 2 settings and then glue the information together into a VPN (crypto map).
We’ll assume the following setup on the Cisco (may not be complete or in the correct order, but at least it shows the networks and the Phase1 & Phase2 settings) :
Name 3.3.3.1 CompanyA_VPN-Netscreen
object-group network CompanyA
network-object 10.1.1.0 255.255.255.0
network-object 2.2.2.1 255.255.255.255
object-group network MyCompany
network-object 192.168.1.0 255.255.255.0
network-object 192.168.2.0 255.255.255.0
access-list NONAT permit ip object-group MyCompany object-group CompanyA
access-list CompanyA permit ip object-group MyCompany object-group CompanyA
crypto map MyVPN 40 ipsec-isakmp
crypto map MyVPN 40 match address CompanyA
crypto map MyVPN 40 set pfs group2
crypto map MyVPN 40 set peer CompanyA_VPN-Netscreen
crypto map MyVPN 40 set transform-set MyVPN
isakmp key AD230LdaiJDIdaz392382 address CompanyA_VPN-Netscreen netmask 255.255.255.255
isakmp policy 10 authentication pre-share
isakmp policy 10 encryption 3des
isakmp policy 10 hash sha
isakmp policy 10 group 2
isakmp policy 10 lifetime 28800
On the Netscreen, you need to do this :
- Create 2 tunnel interfaces and bind them to the correct physical interface
- Set up routing and route traffic to the corresponding tunnel interface
- Create a Phase 1 (Gateway) definition
- Create 4 Phase 2 (Autokey IKE) definitions, bind them to the corresponding tunnel interfaces
- Create network objects (to be used in the policies)
- Create a policy that allows traffic from A-LAN1 to CompanyB
- Create a policy that allows traffic from A-LAN2 and A-LAN3 to CompanyB, with nat src
- Create a policy that allows traffic from CompanyB to A-LAN1
I’ll assume that both firewalls have their default gateways set to the internet router, so they can reach each other over the internet.
Note : Netscreen basics : you can apply a policy to traffic that goes from one zone to another. We have 3 zones : LAN, WAN and Public. We will define the CompanyB networks as part of Public, so we can apply policies and NAT to traffic from LAN and WAN to Public. The VPN Gateway (Phase1) will be bound to the interface in the public zone, because we want to build the tunnel from the public IP of the firewall to the public IP of the Cisco VPN device.
Create tunnel interface
We need to create 2 tunnel interfaces. Since Cisco requires the use of Proxy ID’s on the Netscreen, and since you can only specify one local and one remote network ID in the proxy ID setting, you need to create 2 tunnel interfaces. We will need to perform NAT on traffic coming from the WAN zone, so we need to bind one of the interfaces to the WAN zone interface (so we can enable nat src on that interface). Just make sure to put the two tunnel.x interfaces in the public zone, which is required for routing.
set interface “tunnel.1” zone “Public”
set interface “tunnel.1” ip unnumbered interface ethernet0/2
set interface “tunnel.2” zone “Public”
set interface “tunnel.2” ip unnumbered interface ethernet0/1
Set up routing
Route traffic towards 192.168.1.0/24 to tunnel.1 and route traffic towards 192.168.2.0/24 towards tunnel.2 :
set route 192.168.1.0/24 interface tunnel.1 preference 20 permanent
set route 192.168.2.0/24 interface tunnel.2 preference 20 permanent
(Use the “permanent” keyword to keep the route even when the tunnel appears to be down up)
Create Phase 1 (Gateway) definition
This definition is shared between the individual tunnels, so we only need to create one Phase1 definition
set ike gateway “GW_to_CompanyB_Cisco” address 1.1.1.1 Main outgoing-interface “ethernet0/2” preshare “AD230LdaiJDIdaz392382” proposal “pre-g2-3des-sha”
Create Phase 2 definitions (Autokey IKE)
Since Cisco requires the use of Proxy ID’s, we need to create an autokey IKE definition for each subnet combination. So we need a Phase 2 for
- A-LAN1 to B-LAN1
- A-LAN1 to B-LAN2
- 2.2.2.1 to B-LAN1
- 2.2.2.1 to B-LAN2
Autokey IKE 1
set vpn “A-LAN1_to_B-LAN1” gateway “GW_to_CompanyB_Cisco” no-replay tunnel idletime 0 proposal “g2-esp-3des-sha”
set vpn “A-LAN1_to_B-LAN1” bind interface tunnel.1
set vpn “A-LAN1_to_B-LAN1” proxy-id local-ip 10.1.1.0/24 remote-ip 192.168.1.0/24 “ANY”
Autokey IKE 2
set vpn “A-LAN1_to_B-LAN2” gateway “GW_to_CompanyB_Cisco” no-replay tunnel idletime 0 proposal “g2-esp-3des-sha”
set vpn “A-LAN1_to_B-LAN2” bind interface tunnel.1
set vpn “A-LAN1_to_B-LAN2” proxy-id local-ip 10.1.1.0/24 remote-ip 192.168.2.0/24 “ANY”
Autokey IKE 3
set vpn “A-LAN2_to_B-LAN1_natsrc” gateway “GW_to_CompanyB_Cisco” no-replay tunnel idletime 0 proposal “g2-esp-3des-sha”
set vpn “A-LAN2_to_B-LAN1_natsrc” bind interface tunnel.2
set vpn “A-LAN2_to_B-LAN1_natsrc” proxy-id local-ip 2.2.2.1/32 remote-ip 192.168.1.0/24 “ANY”
Autokey IKE 4
set vpn “A-LAN2_to_B-LAN2_natsrc” gateway “GW_to_CompanyB_Cisco” no-replay tunnel idletime 0 proposal “g2-esp-3des-sha”
set vpn “A-LAN2_to_B-LAN2_natsrc” bind interface tunnel.2
set vpn “A-LAN2_to_B-LAN2_natsrc” proxy-id local-ip 2.2.2.1/32 remote-ip 192.168.2.0/24 “ANY”
Create network objects
set address “LAN” “A-LAN1” 10.1.1.0 255.255.255.0
set address “WAN” “A-LAN2” 10.1.2.0 255.255.255.0
set address “WAN” “A-LAN3” 172.20.0.0 255.255.0.0
set address “Public” “B-LAN1” 192.168.1.0 255.255.255.0
set address “Public” “B-LAN2” 192.168.2.0 255.255.255.0
Create policies
Policy to allow traffic from A-LAN1 to B-LAN1 and B-LAN2 :
set policy from “LAN” to “Public” “A-LAN1” “B-LAN1” “ANY” permit
set policy from “LAN” to “Public” “A-LAN1” “B-LAN2” “ANY” permit
Policy to allow traffic from A-LAN2 and A-LAN3 via nat src to B-LAN1 and B-LAN2 :
set policy from “WAN” to “Public” “A-LAN2” “B-LAN1” nat src permit
set policy from “WAN” to “Public” “A-LAN3” “B-LAN1” nat src permit
set policy from “WAN” to “Public” “A-LAN2” “B-LAN2” nat src permit
set policy from “WAN” to “Public” “A-LAN3” “B-LAN2” nat src permit
Since we have defined the route to B-LAN1 and B-LAN2 to use tunnel.2, and since tunnel.2 uses ethernet0/1 as outgoing interface, then you can use this egress interface IP address to do nat src. If you don’t want to use the IP address of the firewall interface from the WAN zone, but an IP address in that same subnet, you can also create a DIP on tunnel.2 interface, use an IP address in the same subnet (such as 2.2.2.2) and use the dip-id in the policy. Whatever combination you want to make, make sure to bind the tunnel.x interface to the physical interface based on what type of NAT you want to apply to it. The IPSec connection itself will use the egress interface ip of the interface defined in the “gateway” definition, not the tunnel.x interface definition.
Policy to allow traffic from B-LAN1 and B-LAN2 to A-LAN1 :
set policy from “Public” to “LAN” “B-LAN1” “A-LAN1” permit
set policy from “Public” to “LAN” “B-LAN2” “A-LAN1” permit
We don’t want to allow CompanyB to access the other 2 networs (nor the IP of the WAN zone), so we don’t need a policy for that
Troubleshooting VPN connections
You can troubleshoot phase 1 negotiations using syslog and using the following CLI commands :
- get ike cookie
- debug ike detail
First, generate traffic from CompanyA to CompanyB
A “get ike cookie” should return something that looks like this :
Active: 1, Dead: 0, Total 1
182f/0003, 3.3.3.1:500->1.1.1.1:500, PRESHR/grp2/3DES/SHA, xchg(5) (Gw_to_CompanyB_Cisco/grp-1/usr-1)
resent-tmr 16777218 lifetime 28800 lt-recv 28800 nxt_rekey 28757 cert-expire 0
initiator, err cnt 0, send dir 0, cond 0x0
nat-traversal map not available
ike heartbeat : disabled
ike heartbeat last rcv time: 0
ike heartbeat last snd time: 0
XAUTH status: 0
DPD seq local 0, peer -588286858
“debug ike detail” will show this for Phase 1:
## 2007-11-17 14:31:31 : IKE<1.1.1.1> ****** Recv kernel msg IDX-0, TYPE-5 ****** ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ****** Recv kernel msg IDX-0, TYPE-5 ****** ## 2007-11-17 14:31:31 : IKE<1.1.1.1> sa orig index<0>, peer_id<1>. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> isadb get entry by peer/local ip and port ## 2007-11-17 14:31:31 : IKE<1.1.1.1> create sa: 3.3.3.1->1.1.1.1 ## 2007-11-17 14:31:31 : getProfileFromP1Proposal-> ## 2007-11-17 14:31:31 : find profile[0]=<00000005 00000002 00000001 00000002> for p1 proposal (id 5), xauth(0) ## 2007-11-17 14:31:31 : init p1sa, pidt = 0x0 ## 2007-11-17 14:31:31 : change peer identity for p1 sa, pidt = 0x0 ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > create peer identity 0838b0b140 ## 2007-11-17 14:31:31 : peer identity 38b0b140 created. ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > EDIPI disabled ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase 1: Initiated negotiation in main mode. <3.3.3.1 => 1.1.1.1> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct ISAKMP header. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Msg header built (next payload #1) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [SA] for ISAKMP ## 2007-11-17 14:31:31 : IKE<1.1.1.1> auth(1)<PRESHRD>, encr(5)<3DES>, hash(2)<SHA>, group(2) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> xauth attribute: disabled ## 2007-11-17 14:31:31 : IKE<1.1.1.1> lifetime/lifesize (28800/0) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct NetScreen [VID] ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct custom [VID] ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct custom [VID] ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Xmit : [SA] [VID] [VID] [VID] ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Initiator sending IPv4 IP 1.1.1.1/port 500 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Send Phase 1 packet (len=156) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase 2 task added ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ike packet, len 132, action 0 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Catcher: received 104 bytes from socket. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ****** Recv packet if <ethernet2/0> of vsys <Root> ****** ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Catcher: get 104 bytes. src port 500 ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > ISAKMP msg: len 104, nxp 1[SA], exch 2[MM], flag 00 ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Recv : [SA] [VID] ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > extract payload (76): ## 2007-11-17 14:31:31 : IKE<1.1.1.1> MM in state OAK_MM_NO_STATE. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [VID]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Vendor ID: ## 2007-11-17 14:31:31 : 40 48 b7 d5 6e bc e8 85 25 e7 de 7f 00 d6 c2 d3 ## 2007-11-17 14:31:31 : c0 00 00 00 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> receive unknown vendor ID payload ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [SA]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Proposal received: xauthflag b4 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> auth(1)<PRESHRD>, encr(5)<3DES>, hash(2)<SHA>, group(2) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> xauth attribute: disabled ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase 1 proposal [0] selected. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> SA Life Type = seconds ## 2007-11-17 14:31:31 : IKE<1.1.1.1> SA lifetime (TV) = 28800 ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > dh group 2 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> DH_BG_consume OK. p1 resp ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase 1 MM Initiator constructing 3rd message. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct ISAKMP header. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Msg header built (next payload #4) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [KE] for ISAKMP ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [NONCE] ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Xmit : [KE] [NONCE] ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Initiator sending IPv4 IP 1.1.1.1/port 500 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Send Phase 1 packet (len=184) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> IKE msg done: PKI state<0> IKE state<1/0007> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ike packet, len 284, action 0 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Catcher: received 256 bytes from socket. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ****** Recv packet if <ethernet2/0> of vsys <Root> ****** ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Catcher: get 256 bytes. src port 500 ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > ISAKMP msg: len 256, nxp 4[KE], exch 2[MM], flag 00 ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Recv : [KE] [NONCE] [VID] [VID] [VID] [VID] ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > extract payload (228): ## 2007-11-17 14:31:31 : IKE<1.1.1.1> MM in state OAK_MM_SA_SETUP. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [VID]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Vendor ID: ## 2007-11-17 14:31:31 : 12 f5 f2 8c 45 71 68 a9 70 2d 9f e2 74 cc 01 00 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> rcv non-NAT-Traversal VID payload. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [VID]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Vendor ID: ## 2007-11-17 14:31:31 : 09 00 26 89 df d6 b7 12 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> rcv XAUTH v6.0 vid ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [VID]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Vendor ID: ## 2007-11-17 14:31:31 : db bc fe 9d fe 5f 5e 91 c3 f4 47 42 77 8b 58 9a ## 2007-11-17 14:31:31 : IKE<1.1.1.1> rcv non-NAT-Traversal VID payload. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [VID]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Vendor ID: ## 2007-11-17 14:31:31 : 1f 07 f7 0e aa 65 14 d3 b0 fa 96 54 2a 50 01 00 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> rcv non-NAT-Traversal VID payload. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [KE]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> processing ISA_KE in phase 1. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [NONCE]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> processing NONCE in phase 1. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> IKE msg done: PKI state<0> IKE state<1/a00080f> ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > finished job pkaidx <0> dh_len<128> dmax<64> ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > finished job d<27442b6c><3dc804d4><87bfa30b><7323f84e> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> gen_skeyid() ## 2007-11-17 14:31:31 : IKE<1.1.1.1> MM in state OAK_MM_SA_SETUP. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> re-enter MM after offline DH done ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase 1 MM Initiator constructing 5th message. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct ISAKMP header. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Msg header built (next payload #5) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [ID] for ISAKMP ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [HASH] ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ID, len=8, type=1, pro=17, port=500, ## 2007-11-17 14:31:31 : IKE<1.1.1.1> addr=3.3.3.1 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> throw packet to the peer, paket_len=64 ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Xmit*: [ID] [HASH] ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Encrypt P1 payload (len 64) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Initiator sending IPv4 IP 1.1.1.1/port 500 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Send Phase 1 packet (len=68) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ike packet, len 112, action 0 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Catcher: received 84 bytes from socket. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ****** Recv packet if <ethernet2/0> of vsys <Root> ****** ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Catcher: get 84 bytes. src port 500 ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > ISAKMP msg: len 84, nxp 5[ID], exch 2[MM], flag 01 E ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Decrypting payload (length 56) ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Recv*: [ID] [HASH] [VID] ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > extract payload (56): ## 2007-11-17 14:31:31 : IKE<1.1.1.1> MM in state OAK_MM_KEY_EXCH. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [VID]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Vendor ID: ## 2007-11-17 14:31:31 : af ca d7 13 68 a1 f1 c9 6b 86 96 fc 77 57 01 00 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [ID]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ID received: type=ID_IPV4_ADDR, ip = 1.1.1.1, port=500, protocol=17 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ID processed. return 0. sa->p1_state = 2. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [HASH]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ID, len=8, type=1, pro=17, port=500, ## 2007-11-17 14:31:31 : IKE<1.1.1.1> addr=1.1.1.1 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> completing Phase 1 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> sa_pidt = 38b0b140 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> found existing peer identity 38b0b698 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> peer_identity_unregister_p1_sa. ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > delete peer identity 0x38b0b140 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> peer_idt.c peer_identity_unregister_p1_sa 509: pidt deleted. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase 1: Completed Main mode negotiation with a <28800>-second lifetime.
Phase 1 needs to work before you can look at Phase 2. If you do not get a valid Phase 1 negotiation, there’s no reason to start looking at Phase 2 problems. You can troubleshoot Phase 2 using syslog as well as the following CLI commands :
- get sa active
- debug ike detail
In Syslog, you will see these messages when you attempt to access resources over a IPSec tunnel :
Nov 17 14:18:07 netscreen.domain.com: NetScreen device_id=netscreen [Root]system-information-00536: IKE<3.3.3.1> >> <1.1.1.1> Phase 1: Initiated negotiations in main mode. (2007-11-17 14:18:07)
Nov 17 14:18:07 netscreen.domain.com: NetScreen device_id=netscreen [Root]system-information-00536: IKE<1.1.1.1> Phase 1: Completed Main mode negotiations with a <28800>-second lifetime. (2007-11-17 14:18:07)
Nov 17 14:18:07 netscreen.domain.com: NetScreen device_id=netscreen [Root]system-information-00536: IKE<1.1.1.1> Phase 2: Initiated negotiations. (2007-11-17 14:18:07)
Nov 17 14:18:07 netscreen.domain.com: NetScreen device_id=netscreen [Root]system-information-00536: IKE<1.1.1.1> Phase 2 msg ID
This indicates that both Phase1 and Phase2 have been successfully negotiated.
If you get messages that looks like this, then you need to check your proxy ID settings :
Nov 17 14:24:58 netscreen.domain.com: NetScreen device_id=netscreen [Root]system-information-00536: IKE<1.1.1.1>: Received a notification message for DOI <1> <18>
Nov 17 14:24:58 netscreen.domain.com: NetScreen device_id=netscreen [Root]system-information-00536: IKE<1.1.1.1> Phase 2: No policy exists for the proxy ID received: local ID (<0.0.0.0>/<255.255.0.0>, <0>, <0>) remote ID (<192.168.1.0>/<255.255.255.0>, <0>, <0>). (2007-11-17 14:21:45)
Nov 17 14:24:58 netscreen.domain.com: NetScreen device_id= netscreen [Root]system-information-00536: Rejected an IKE packet on ethernet2/0 from 3.3.3.1:500 to 1.1.1.1:500 with cookies fea6d5d4514bf8cc and 6eb4f79ad6050aa5 because the peer sent a proxy ID that did not match the one in the SA config. (2007-11-17 14:43:14)
A “debug ike detail” will show this for a successful Phase 2 negotiation :
## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase 2: Initiated Quick Mode negotiation. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase-2: start quick mode negotiation ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase-2: no change in Modecfg IPv4 address for tunnel ifp. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Create conn entry... ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ...done(new 77d189f0) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Initiator not set commit bit on 1st QM. ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > dh group 2 ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > add sa list for msg id <77d189f0> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> 0,0/0(0)/spi(d521a21f)/keylen(0) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct ISAKMP header. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Msg header built (next payload #8) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [HASH] ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [SA] for IPSEC ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Set IPSEC SA attrs: lifetime(3600/0) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> atts<00000003 00000000 00000003 00000002 00000001 00000002> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> proto(3), esp(3) , auth(2) , encap(1) , group(2) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Before NAT-T attr unmap: private tunnel = 1. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> After NAT-T attr unmap: private tunnel = 1. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Policy have separate SA. Use P2 ID from policy sa (12). ## 2007-11-17 14:31:31 : IKE<10.1.1.0> IP<10.1.1.0> mask<255.255.255.0> prot<0> port<0> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Initiator P2 ID built: ## 2007-11-17 14:31:31 : IKE<192.168.1.0> IP<192.168.1.0> mask<255.255.255.0> prot<0> port<0> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Responder P2 ID built: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [NONCE] for IPSec ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [KE] for PFS ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [ID] for Phase 2 ## 2007-11-17 14:31:31 : id payload constructed. type(4),ip(00001dac),mask(0000ffff), prot(0), port(0) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [ID] for Phase 2 ## 2007-11-17 14:31:31 : id payload constructed. type(4),ip(002110ac),mask(00ffffff), prot(0), port(0) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> construct QM HASH ## 2007-11-17 14:31:31 : IKE<1.1.1.1> need to wait for offline p2 DH work done. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> IKE msg done: PKI state<0> IKE state<3/182f> ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > finished job pkaidx <0> dh_len<128> dmax<64> ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > finished job d<76cd1846> <39eb1d71><22e81049> ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > BN, top32 dmax64 zero ## 2007-11-17 14:31:31 : IKE<1.1.1.1> construct QM HASH ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Xmit*: [HASH] [SA] [NONCE] [KE] [ID] [ID] ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Encrypt P2 payload (len 296) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Initiator sending IPv4 IP 1.1.1.1/port 500 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Send Phase 2 packet (len=300) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ike packet, len 320, action 0 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Catcher: received 292 bytes from socket. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ****** Recv packet if of vsys ****** ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Catcher: get 292 bytes. src port 500 ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > ISAKMP msg: len 292, nxp 8[HASH], exch 32[QM], flag 01 E ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Decrypting payload (length 264) ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Recv*: [HASH] [SA] [NONCE] [KE] [ID] [ID] ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > extract payload (264): ## 2007-11-17 14:31:31 : IKE<1.1.1.1> QM in state OAK_QM_SA_ACCEPT. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [SA]: ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > Check P2 Proposal ## 2007-11-17 14:31:31 : IKE<1.1.1.1> SA life type = seconds ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > SA life duration (TV) = 3600 ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > PFS group = 2 ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > encap mode from peer = 1. ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > encap mode after converting it to private value = 1. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase 2 received: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> atts<00000003 00000000 00000003 00000002 00000001 00000002> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> proto(3) , esp(3) , auth(2) , encap(1) , group(2) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> P2 proposal [0] selected. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [KE]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> processing ISA_KE for PFS in phase 2. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [NONCE]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> processing NONCE in phase 2. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [ID]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Process [ID]: ## 2007-11-17 14:31:31 : IKE<1.1.1.1> IKE msg done: PKI state<0> IKE state<3/182f> ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > finished job pkaidx <0> dh_len<128> dmax<64> ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > finished job d<1fce18cb><5192d6b0> <6005d373> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> re-enter QM after offline DH done ## 2007-11-17 14:31:31 : IKE<1.1.1.1> xauth_cleanup() ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Done cleaning up IKE Phase 1 SA ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Start by finding matching member SA (verify 0/0) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Verify sa: index 0 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> IKE: Matching policy: gw ip <1.1.1.1> peer entry id<0> ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > protocol matched expected<0>. ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > port matched expect<0>. ## 2007-11-17 14:31:31 : ipvx = IPV4 ## 2007-11-17 14:31:31 : rcv_local_addr = 10.1.1.0, rcv_local_mask = 255.255.255.0, p_rcv_local_real = 10.1.1.0 ## 2007-11-17 14:31:31 : rcv_remote_addr = 192.168.1.0, rcv_remote_mask = 255.255.255.0, p_rcv_remote_real = 192.168.1.0 ## 2007-11-17 14:31:31 : ike_p2_id->local_ip = 10.1.1.0, cfg_local_mask = 255.255.255.0, p_cfg_local_real = 10.1.1.0 ## 2007-11-17 14:31:31 : ike_p2_id->remote_ip = 192.168.1.0, cfg_remote_mask = 255.255.255.0, p_cfg_remote_real = 192.168.1.0 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Proxy ID match: Located matching Phase 2 SA <12>. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> sa ID for phase 2 sa is <12>. IP version is 4. ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > life (sec or kb): lcl 3600, peer 3600, set 3600. ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > life (sec or kb): lcl 0, peer 0, set 0. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> gen_qm_key() ## 2007-11-17 14:31:31 : IKE<1.1.1.1> load_sa_keys(): enter. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> gen_qm_key() ## 2007-11-17 14:31:31 : IKE<1.1.1.1> load_sa_keys(): enter. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> ikmpd.c 3668. sa ID for phase 2 sa is <12>. IP version is 4. ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > spi hash node removed: type<2>,spi ,ip<3.3.3.1> ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > spi hash node removed: type<2>,spi<2e340d5a>,ip<1.1.1.1> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> clean_all_sa_state_node_from_list-> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> no relocate earlier SA-state, not active. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> key_modify: sa index <0> bk_idx <0>. ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > insert_sa_state_to_spi_hash spi<1fa221d5>, sa_index<0>, Incoming ## 2007-11-17 14:31:31 : IKE<0.0.0.0 > insert_sa_state_to_spi_hash spi<34b48a1e>, sa_index<0>, Outgoing ## 2007-11-17 14:31:31 : IKE<1.1.1.1> crypto_ctx 22, 8, 24, 8, 0, 0, 16, 0, 12, 48 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> modify esp tunnel: src (peer) ipv4 <1.1.1.1> ## 2007-11-17 14:31:31 : IKE<1.1.1.1> modifying esp tunnel: self ## 2007-11-17 14:31:31 : IKE<1.1.1.1> update auto NHTB status for sa 0 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> after mod, out nsptunnel <05258b58>. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase 2 msg-id : Completed Quick Mode negotiation with SPI <1fa221d5> , tunnel ID <12>, and lifetime <3600> seconds/<0> KB. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Application sa installed. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Phase 2 Initiator constructing 3rd(last) message. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> oakley_final_qm():enter ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct ISAKMP header. ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Msg header built (next payload #8) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Construct [HASH] in QM ## 2007-11-17 14:31:31 : IKE<1.1.1.1> oakley_final_qm():exit ## 2007-11-17 14:31:31 : IKE<1.1.1.1 > Xmit*: [HASH] ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Encrypt P2 payload (len 52) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Initiator sending IPv4 IP 1.1.1.1/port 500 ## 2007-11-17 14:31:31 : IKE<1.1.1.1> Send Phase 2 packet (len=60) ## 2007-11-17 14:31:31 : IKE<1.1.1.1> oakley_process_quick_mode():exit ## 2007-11-17 14:31:32 : IKE<0.0.0.0 > dh group 2 ## 2007-11-17 14:31:32 : IKE<1.1.1.1> nhtb_list_update_status: vpn A-LAN1_to_B-LAN1 ## 2007-11-17 14:31:32 : IKE<1.1.1.1> ** link ready return 8 ## 2007-11-17 14:31:32 : IKE<1.1.1.1> sa_link_status_for_tunl_ifp: saidx 2, preliminary status 8 ## 2007-11-17 14:31:32 : IKE<1.1.1.1> nhtb_list_update_status: vpn A-LAN1_to_B-LAN1 ## 2007-11-17 14:31:32 : IKE<1.1.1.1> ** link ready return 8 ## 2007-11-17 14:31:32 : IKE<1.1.1.1> sa_link_status_for_tunl_ifp: saidx 1, preliminary status 8 ## 2007-11-17 14:31:32 : IKE<1.1.1.1> nhtb_list_update_status: vpn A-LAN1_to_B-LAN1 ## 2007-11-17 14:31:32 : IKE<1.1.1.1> ** link ready return 8 ## 2007-11-17 14:31:32 : IKE<1.1.1.1> sa_link_status_for_tunl_ifp: saidx 0, preliminary status 8 ## 2007-11-17 14:31:32 : IKE<0.0.0.0 > finished job pkaidx <0> dh_len<128> dmax<64> ## 2007-11-17 14:31:32 : IKE<0.0.0.0 > finished job d <693fdcc4><479bfd9c> ## 2007-11-17 14:31:32 : IKE<0.0.0.0 > BN, top32 dmax64 zero
Quick note on syslog
if you have a Linux box, then you can use the built-in syslog features. If you are using Windows, you can download a free syslog daemon from http://support.3com.com/software/utilities_for_windows_32_bit.htm (Look for 3CDaemon)
Once you have the syslog engine running, configure the netscreen to use syslog :
set syslog config “ip_of_syslog_server” facilities local0 local1
set syslog src-interface ethernet0/0
set syslog enable
Good luck !
© 2007 – 2019, Peter Van Eeckhoutte (corelanc0d3r). All rights reserved.