6,605 views
 HITB2014AMS – Day 2 – On Her Majesty’s Secret Service: GRX & A Spy Agency
HITB2014AMS – Day 2 – On Her Majesty’s Secret Service: GRX & A Spy Agency
Last year, Belgacom got hacked by an intelligence service (GCHQ?), Rob says. “What is so interesting about this hack, why did they hack into Belgacom, what would or could be the purpose of a similar hack?” Before answering those questions, we need to take a quick look on how mobile networks work and how mobile data travels the network.

Mobile data
In a mobile data network, it’s necessary to know where you are. KPN has about 5000 cells throughout the country, and each site has a Cell Identifier (CI). To group them together, an RAC (Route Area Code) is used. Every country has its own unique number. MCC 204, for example, corresponds with The Netherlands. Additionally, each provider has a unique number.
To access the network, you need an APN (Access Point Name), an IMSI (International Mobile Subscriber Identify) and an UICC (Universal Integrated Circuit Card), which is stored on the SIM card. From a network perspective, Rob explains, even more components are needed and used. Radio (BTS/nodeB), a Home Location Register, a Service GPRS Support Node (SGSN), a Gateway GPRS Support Node and DNS servers are needed to provide connectivity.
When the phone sends a data packet, it will hit the data network first. The packet reaches the SGSN/S-GW and gets authenticated (HLR/HSS). After successful authentication, the device will resolve the APN name (using DNS). Traffic is then sent to a gateway, and everything behind the gateway is plain TCP/IP.
To make sure all devices can use their own tunnel, GPRS Tunneling protocol was created, Rob explains, to allow devices to have their own GPRS tunnel. The protocol (GTPv0 GPRS, GTPv1 GPRS/UMTS, GTPv2 LTE) is based on UDP. The GTP specification can be found at http://www.3gpp.org/DynaReport/29060.htm
When a telco gets hacked, there are a number of fields in the GPRS protocol that may be interesting for hackers. The IMSI may be interesting, the APN (if it’s hidden) and some other information such as MCC, MNC, LAC, CI and IMEI.
Roaming Mobile data
The setup for Mobile roaming is quite similar to a domestic setup. A device first connects to a local network and the local SGSN will connect to the HLR of the home country to authenticate the device. After authentication, traffic is sent to the gateway in the home country…. and to make that happen, the operators use GRX (GPRS Roaming Exchange). GRX is a concept based on GSMA, but *should* be segmented/isolated from the rest of the network. To understand why access to GRX traffic could be interesting to spy agencies, Stephen continues, we need to look at what the GTP traffic looks like and what is inside the packets.
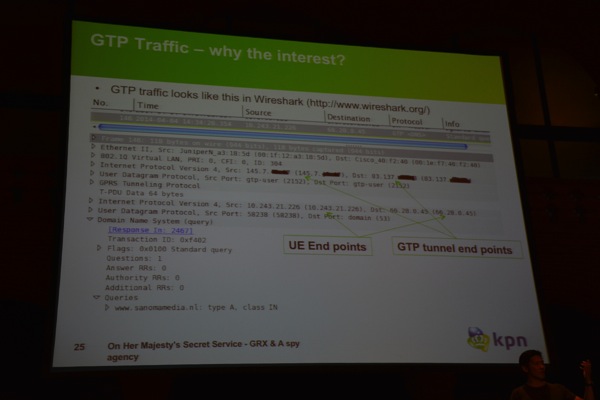
Most of the current network analyzers don’t really understand GTP (except for Telco specific ones), so Wesley (one of the people in the KPN Cert team) wrote a script to strip the GTP headers and dissect the traffic. The script identifies the link layer header, detects the VLAN tag, checks for the IP/UDP Header etc… basically allowing the researchers to load the stripped PCAP file into NetworkMiner (http://www.netresec.com/?page=NetworkMiner) and examine the actual GTP traffic contents. This also means that you can see all cleartext traffic (including credentials etc). Being able to get access to GRX traffic can clearly be very valuable to spy agencies.
Additionally, since the GTP headers contain location information, spies can use the traffic to gather information on where somebody is. www.numberingplans.com is a website that allows you to perform analysis of an IMEI number, including displaying information about the device. http://unwiredlabs.com/api can be used to get location information.
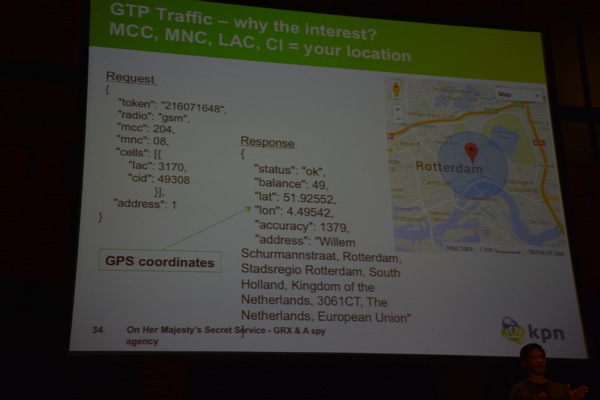
Long story short, getting access to GRX traffic is a big deal and an obvious goal for spies and attackers in general.
Getting access to the GRX network ?
How easy would it be to get GRX access, providing that you are not an operator/telco, Stephen wonders. To determine how easy it would be, they used the “kill-chain” methodology, which is a typical penetration testing approach. They started the audit by looking at the GRX BGP Routing table (MNO’s) and identified 4,8K subnets (320K IP addresses). Next, they performed a “masscan” against all of the IPs (limited port scan) and performed a GTP ping (UDP 2152, 2123) using zmap, allowing them to discover all GTP enabled devices. Going forward, they used SGSNEMU (part of OpenGGSN) to attempt to connect to GGSN, perform ping requests, create PDP context, and forward packets to connections on Gn/Gp interfaces.
Next, they attempted to discover the DNS servers used by the various telcos, which is used by GRX to resolve the APN in order to set up the GTP tunnel. Most operators seem to be running (mostly) Bind and Microsoff DNS, with some of the discovered Bind versions appeared to be quite old and vulnerable to DoS attacks.
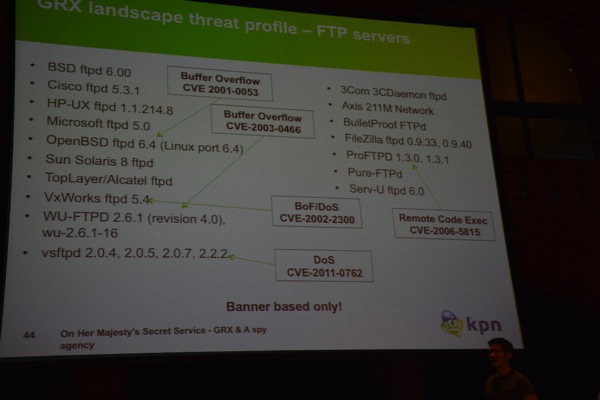
Additionally, they performed a scan for SMTP servers inside the network and discovered a wide variety of servers (Exim, Microsoft, Sendmail, qmail, etc). It is unclear why these SMTP servers are present on the network. Next, they performed an FTP scan, Telnet scan, SMB scan, SNMP probing etc… and they detected old & vulnerable versions of all kinds of servers and daemons. In other words, the GRX network does not only contain GRX related devices. In short, it doesn’t seem to be a dedicated/isolated network at all.
Even worse, out of the 42K GRX live hosts, 5.5K hosts from 15 operators were reachable from the internet. So, if one of the vulnerable machines, connected to the internet, gets compromised, it could be used to get inside the GRX network. None of the found devices should have been reachable from the internet in the first place.
Going back to the Belgacom hack, it appears that the breach was based on a direct attack against administrators, instead of compromising external machines. This either means that Belgacom didn’t have any exposed systems, the exposed Belgacom systems (if any) were protected well, or perhaps the type of access that could be gained by hacking a vulnerable servers was too limited. By attacking an administrator, hackers would get access to a lot more internal systems right away.
GRX traffic is definitely interesting. It has information on who you are and where you are and what you do. It should have been isolated from other networks but that is not the case. GRX traffic can definitely be interesting to attackers and spy agencies. To prevent issues, operators could:
- Remove GRX prefixes from the BGP tables
- Use BGP authentication
- Configure routers to only import specific prefixes from specific AS numbers with roaming agreements
- Perform ingress filtering (BGP sessions, block spoofed IP addresses, allow GTP, DNS, ICMP… basically apply “least possible privilege” access lists)

About the speakers
Stephen Kho is a penetration tester within the CISO team of the Netherland’s largest telecoms provider KPN. He has been a professional pentester for over 10 years and has experience in security testing across several domains including network infrastructure, VoIP, ICS/SCADA and web application. He presented a technical briefing entitled, “Securing Unified Communications – Vulnerability Analysis and Best Practises” at UC Expo 2009 in London. More recently, he has been active in the areas of 3G & 4G mobile communication security testing and this work led to a presentation titled “4G LTE security – what a hacker knows and doesn’t want you to know?” at the OHM 2013 Security conference which he was a co-author & presenter. Stephen’s current research is focussed on the area of GRX (GPRS Roaming eXchange) networks security.
Rob Kuiters works as an incident response handler in the CISO team at KPN, the largest telecoms provider in the Netherlands. He has been involved in mobile networks from the very early start of GSM in the Netherlands. In 2007 he joined KPN-CERT as a technical mobile security specialist. The main focus of Rob’s work is currently still in mobile networking. His research on the new 4G mobile network contributed to the talk “4G LTE security – what a hacker knows and doesn’t want you to know?” at OHM 2013 Security Conference which he was a co-author & presenter. The main areas of his current research is GRX (GPRS Roaming Exchange) and signalling networks security.
© 2014, Peter Van Eeckhoutte (corelanc0d3r). All rights reserved.

